This was just about the easiest box I have seen. Once the Docker spun up I ran nmap and gobuster. Nmap only found port 22 and 80 open.
┌──(kali㉿kali)-[~]└─$ nmap 10.10.74.217 -sC -sVStarting Nmap 7.93 ( https://nmap.org ) at 2023-03-28 05:52 PDTNmap scan report for 10.10.74.217Host is up (0.15s latency).Not shown: 998 closed tcp ports (conn-refused)PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)| ssh-hostkey:| 3072 316212daabd7a9dd08220a7dabf2ecc1 (RSA)| 256 2dc5fa0a71a1fb32afbb6ba3f53ab8a4 (ECDSA)|_ 256 238e09f31d5f70ec8e54286bcc8d3239 (ED25519)80/tcp open http Apache httpd 2.4.48 ((Ubuntu))|_http-title: CyberHeros : Index|_http-server-header: Apache/2.4.48 (Ubuntu)Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.25 secondsI let Gobuster run in the background while I viewed the page source. The index page had nothing to really see.
So of course my eye went to the log in page. I clicked on it and was greeted with a log on it. So force of habit I inspeced that page as well. Website login in page.
http://10.10.*.*/login.html
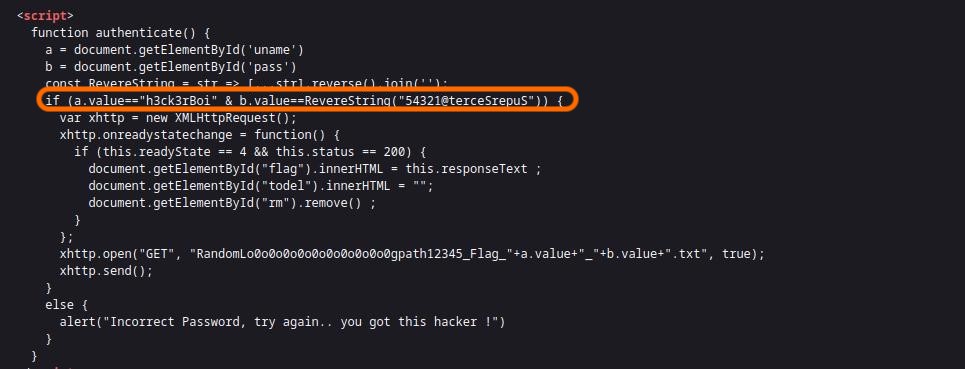
Basically it says that if the value of a(uname) is equal to h3ck3rBoi and value b(password) is equal to 54321@terceSrepuS reversed then show the flag. I just typed it out in reverse. Although you can use rev from the cli.
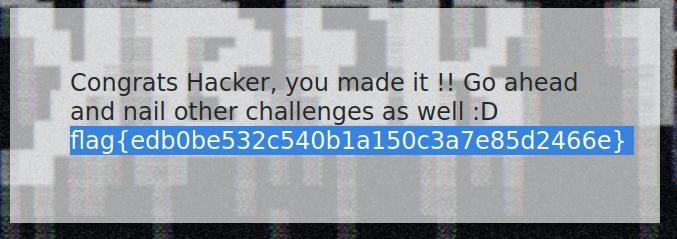
Quesiton 1: flag{edb0be532c540b1a150c3a7e85d2466e}
Facebook
Twitter
LinkedIn