Link to TryHackMe Investigating Windows
Question 1: What is the version and year of the Windows machine?
Opening up the command prompt and running this command winver Showed me it was running Windows Server 2016
Answer: Windows Server 2016
Question 2: What user logged in last?
I checked Event Viewer>Windows Logs>Security Then set a custom view for Task Category = Logon (Event ID 4624)
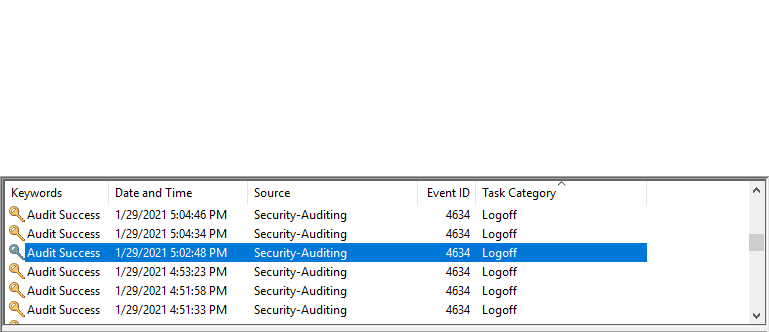
This showed me that the last user was Administrator
Answer: Administrator
Question 3: When did John log onto the system last?
I opened up Powershell and ran this command: -Get-WinEvent -LogName Security | Where-Object { $_.Id -eq 4624 -and $_.Message -match “John” } | Select-Object -First 1
This command checks the event viewer logs under security where the type is equal to 4624 which is the logon event. Matching John as the user and the only returning the last result
Answer format: MM/DD/YYYY H:MM:SS AM/PM
Answer: 03/02/2019 5:48:32 PM
Question 4: What IP does the system connect to when it first starts?
I restarted the VM and ran this command in command prompt:
netstat -ano
Answer: 10.34.2.3
Question 5: What two accounts had administrative privileges (other than the Administrator user)?
In Powershell I ran Get-LocalGroupMember -Group “Administrators” This gets all member of the administrators group.
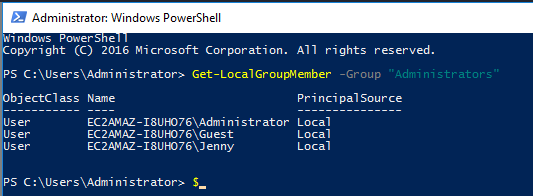
Answer: Guest, Jenny
Question 6: Whats the name of the scheduled task that is malicious.
I ran this Powershell command but got a lot of results Get-ScheduledTask | Select TaskName, TaskPath, State
So, instead, I opened Task Scheduler and found the answer.
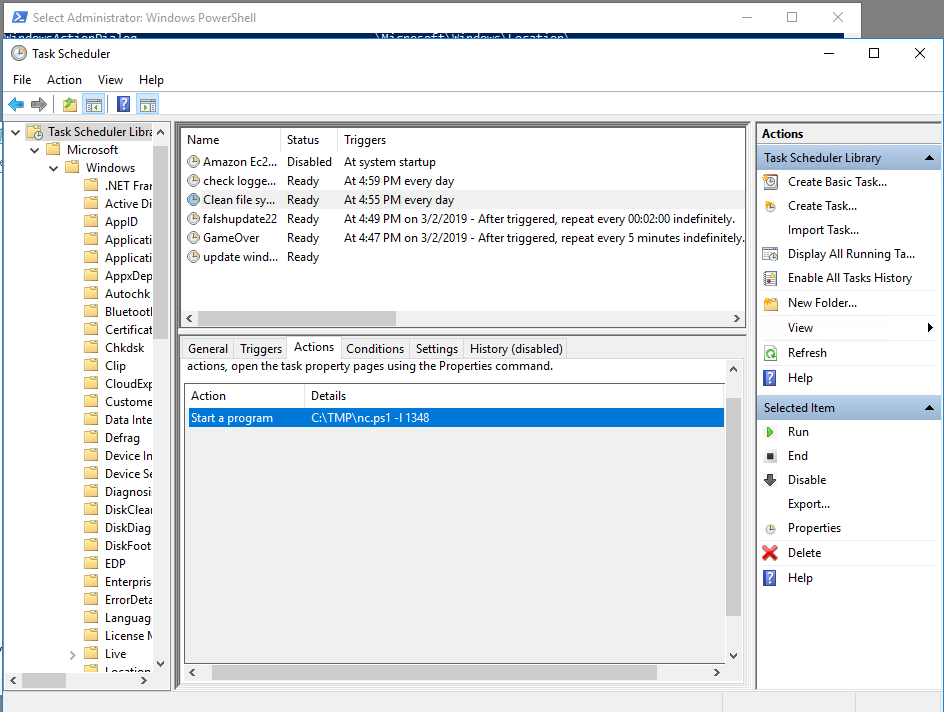
Answer: Clean file system
Question 7: What file was the task trying to run daily?
The answer was found in the previous question.
Answer: nc.ps1
Question 8: What port did this file listen locally for?
Once again, the answer can be found in Task Scheduler. C:\TMP\nc.ps1 -i 1348 The arguments show port 1348
Answer: 1348
Question 9: When did Jenny last log on?
This one was a bit tricky, so I ran commands for both Powershell and Command Prompt.
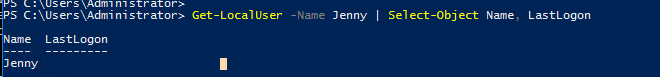
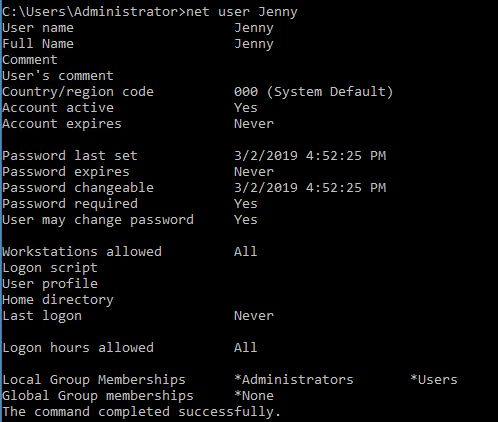
I tried, never expecting it to work, and I was missing a piece.
Answer: Never
Question 10: At what date did the compromise take place?
I used Event Viewer to find when a user was created Event ID 4720
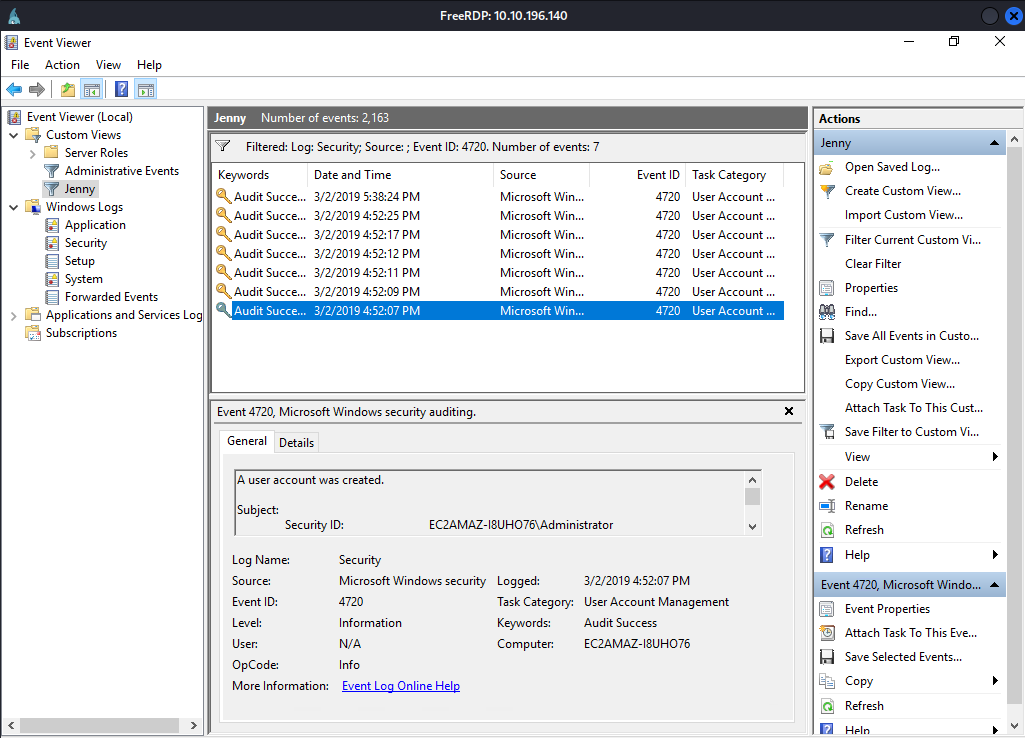
Answer: 03/02/2019
Question 11: During the compromise, at what time did Windows first assign special privileges to a new logon?
I knew the attack was on 3/29, so I created a custom view to search for events with the special logon Event ID 4672. To be honest, I was not sure which one it was, as they all looked to have permissions upgraded. But using the hint on the question, I was about to find it
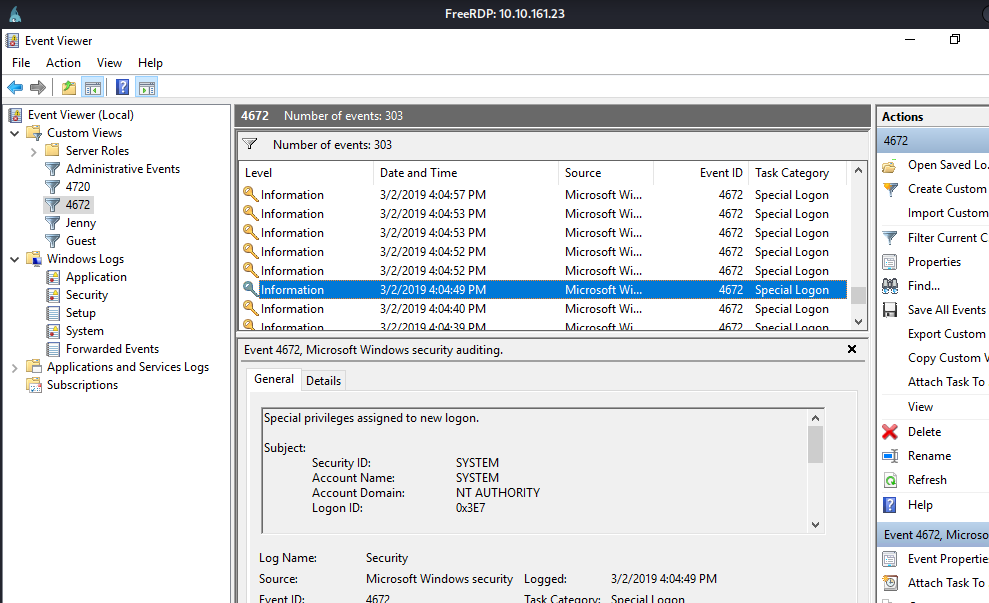
Answer format: MM/DD/YYYY HH:MM:SS AM/PM
Answer: 03/02/2019 4:04:49 PM
Question 12: What tool was used to get Windows passwords?
What tool was used to get Windows passwords?
While on the machine, there were a ton of PowerShell and cmd prompts opening, all pointing to something running from C:\TMP. I opened up Explore and found all the tasks that were used, including an exe with the name mim.exe. Also, a text file with the name of mim-out Opening showed me that Mimikatz was being used.
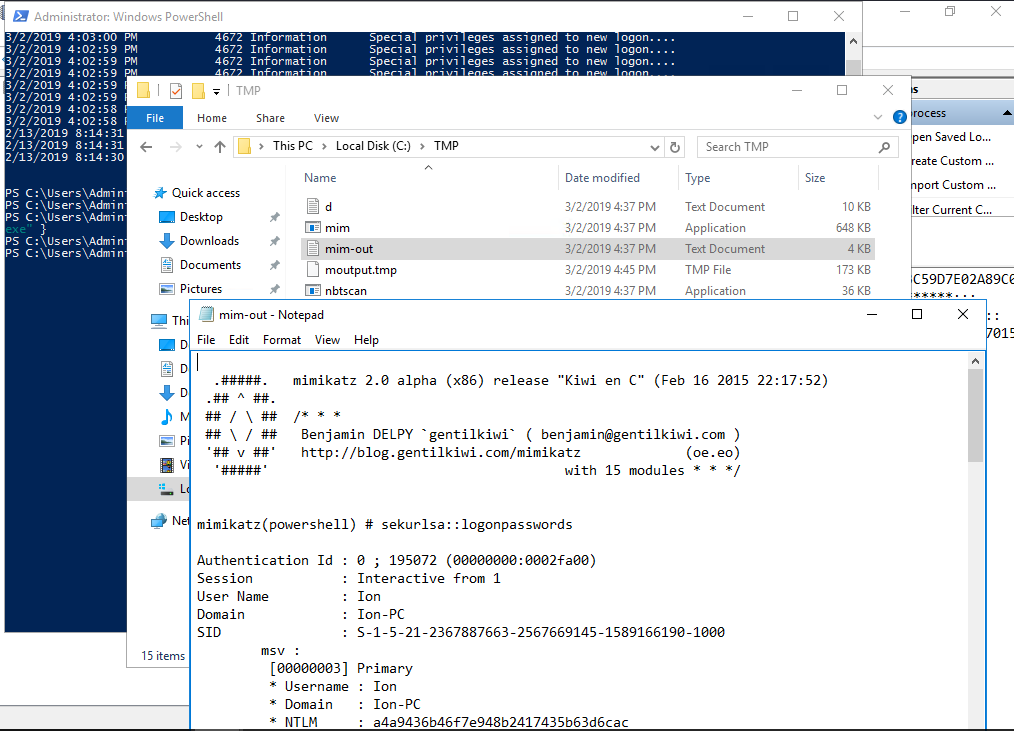
Answer MiniKatz
Question 13: What was the attackers external control and command servers IP?
Running in Powershell
ipconfig /displaydns
It brought up this list, and the last record seemed really odd to me, so I tried it, and it was the correct answer.
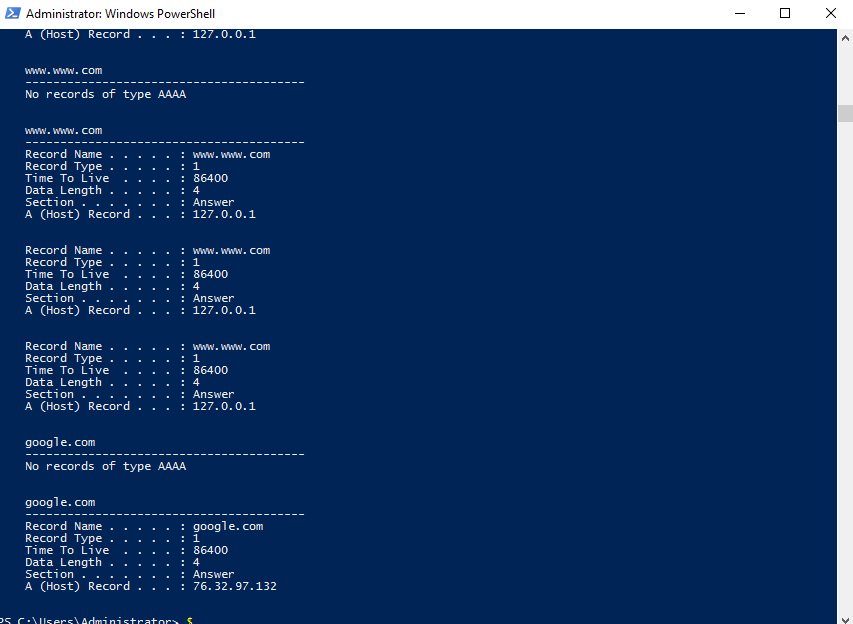
Answer: 76.32.97.132
Question 14: What was the extension name of the shell uploaded via the servers website?
What was the extension name of the shell uploaded via the server’s website?
Looking in the webserver’s directory we see .jsp
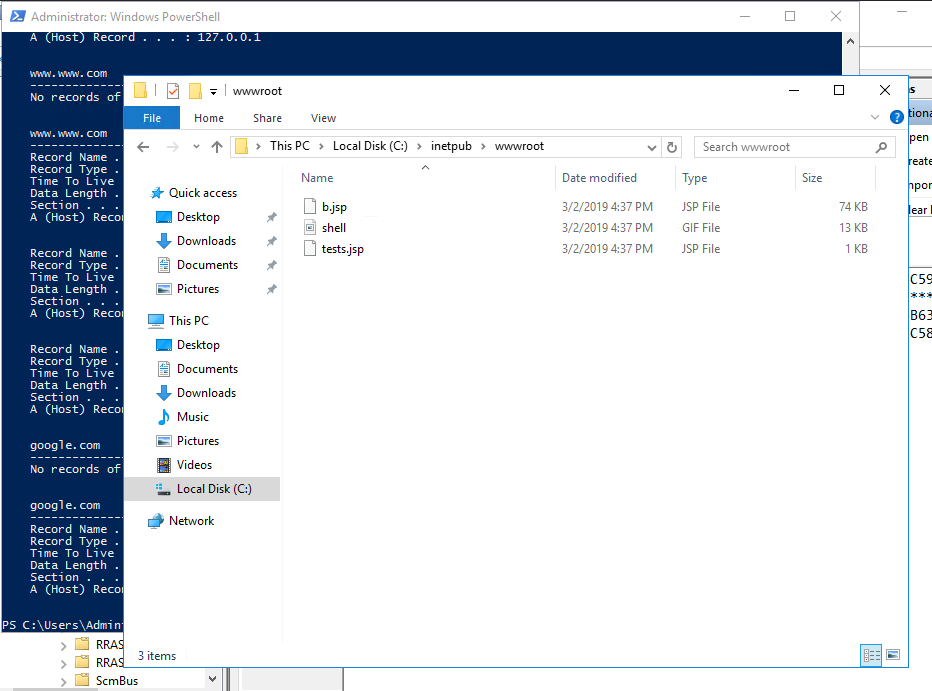
Answer: .jsp
Question 15: What was the last port the attacker opened?
I opened Windows Firewall, checked the inbound rules, and found the first rule. Leet port, anyone?
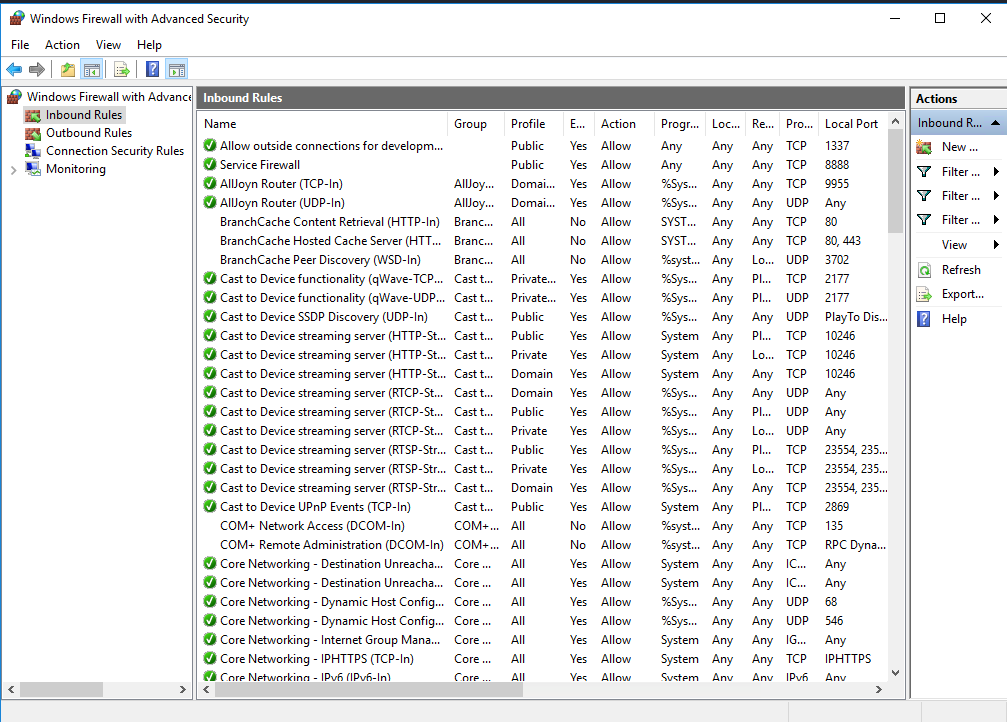
Answer: 1337
Question 16: Check for DNS poisoning, what site was targeted?
We found this with our previous answer, looking for the IP for the C2
Answer: google.com
Conclusion
Attack Timeline:
- 03/02/2019 4:04:49 PM → Privilege escalation occurred.
- 03/02/2019 5:48:32 PM → John last logged in.
- Mimikatz (
mim.exe) dumped passwords. - Netcat (
nc.ps1) opened a reverse shell. - C2 Server:
76.32.97.132. - Malicious task (
clean) ran daily to maintain access. - Port 1337 was used for backdoor access.
This was a great forensic case study in Windows incident response, privilege escalation, and attack persistence.